Phishing: How to Protect Yourself from Fraudulent Emails
What is Phishing?
"Phishing" scams are the use of fraudulent emails or other solicitations to lure users into sharing personal information that can be used for identity theft or other illegal activities. These messages often ask users to enter their sensitive information at a fake website that purports to belong to a legitimate organization.
NEW! Download and print our handout: Don't Get Phished!

How Can I Tell If an Email is Phishing?
- Check the actual email address by clicking the display name in the message header. More often than not the message will come from an external email address. The display name may reflect the name of an actual Western employee, but the actual email address will come from the outside.
- Western email addresses always send in the following format: username@wwu.edu. Fraudulent messages may appear to come from username.wwu.edu@gmail.com or FirstName.LastName@yahoo.com (the messages may be sent from any external host. Gmail and Yahoo are just used as examples).
- This isn't a perfect indicator, because it is easy to make an email look like it was sent by a legitimate @wwu.edu address when it was actually sent from outside of our email environment. Fortunately modern email systems like ours are getting better at alerting you when an email address says it came from @wwu.edu but was actually sent from the outside.
- It's NOT legitimate if they ask for passwords or sign-in information. No legitimate business (WWU, banks, eBay, etc.) will ever contact you and require that you share your personal information (bank numbers/PIN, security questions, passwords, etc.)
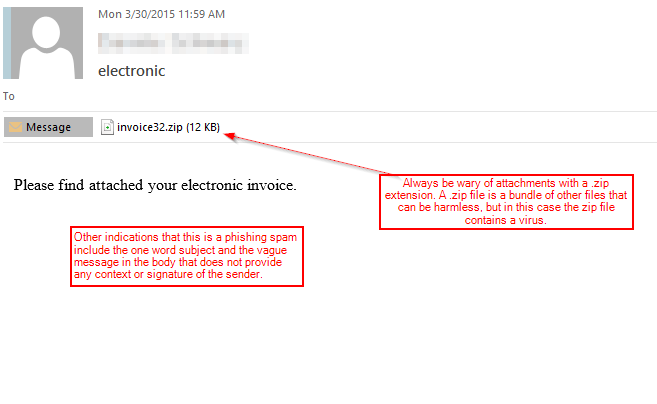
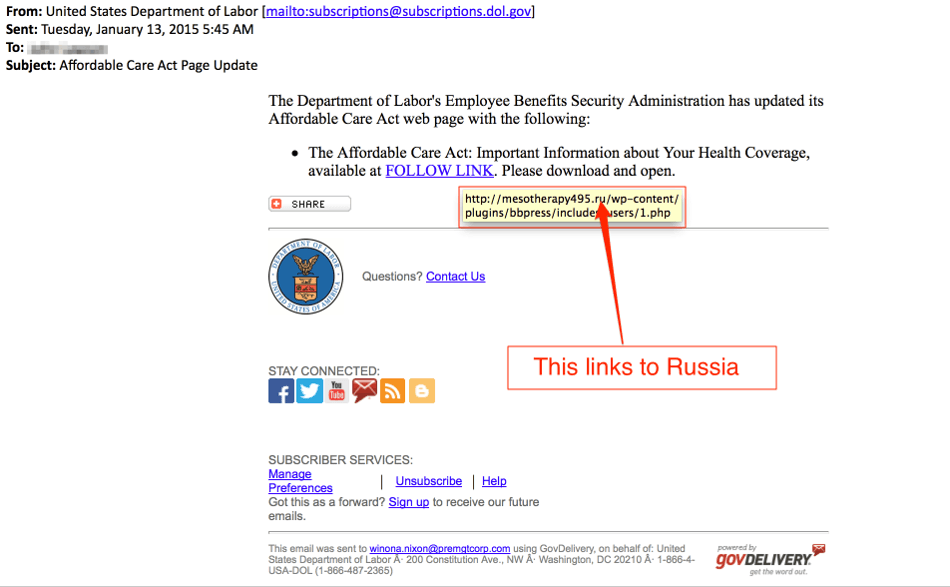
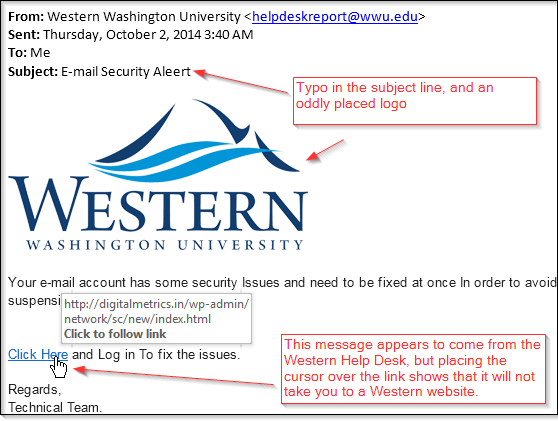
- Often a fraudulent email will have graphics, URLs, or grammar that is not quite right. See examples below for fraudulent attempts to masquerade as legitimate businesses. Hovering the cursor over a link will expose the URL - if this doesn't match the link name that is a clue that the sender is hiding something.
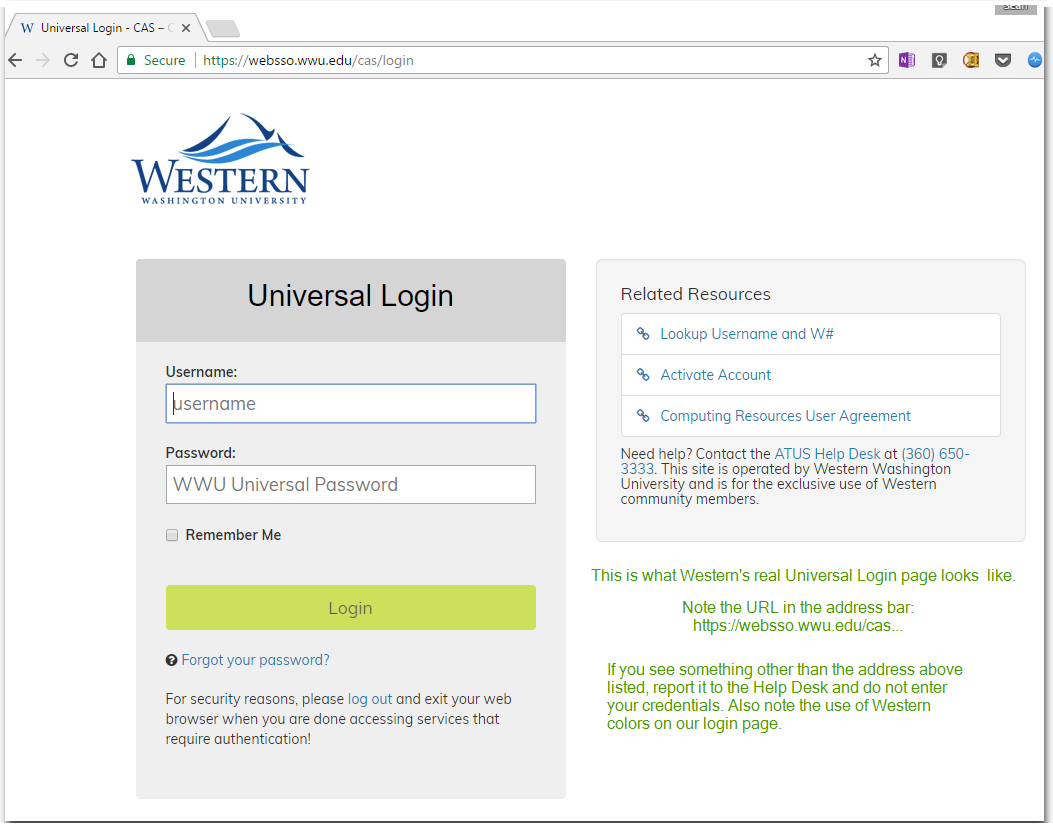
- Become familiar with what the real Universal Login page for Western looks like, so you can more easily recognize a fraudulent copy. NOTE: This is not the only legitimate Western login page, but it is one that scammers frequently try to replicate. We also regularly sign-in to Microsoft's Office 365 page with our Western credentials.
You will also encounter our Microsoft Office 365 sign-in pages when you sign-in to Office 365 apps, Canvas, G Suite, or other apps that are authenticated through Microsoft's single-sign-on service.
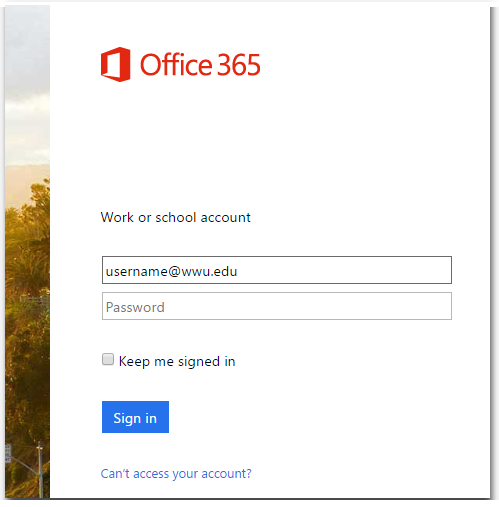
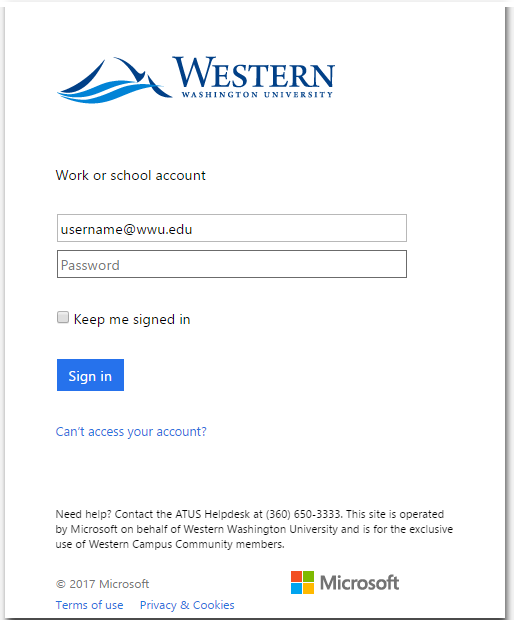
These are both legitimate sign-in pages for Office 365. When you enter your username@wwu.edu on the Microsoft sign-in page, your browser will be redirected to the WWU branded Microsoft sign-in page shown on the right.
What Should I do with a Fraudulent Email?
- Report the message to Microsoft for review.
- DO NOT click on anything in the email. If you think it might be legitimate, go to a web browser and TYPE IN the URL of your bank or whatever business is supposedly contacting you.
- If you are not certain about the email, contact the ATUS Help Desk.
Example of Fraudulent Emails and How You Could Detect Them
These are recent examples of phishing scams that have been reported to the Help Desk. This list does not include every example of reported phishing, but it does include some of the most frequently reported or most convincing. We have highlighted the most suspicious components in the examples, but in many cases the copy you receive may have the same text but will come from a different sender. These messages are often riddled with misspelled words and grammatical errors, but some of them are carefully crafted and quite convincing.